Key takeaways:
- What is the core of risk management? It involves identifying, tracking, and managing potential risks to enhance project success.
- Why is risk identification crucial? It’s the first step in risk management, helping to anticipate challenges before they arise.
- What techniques can aid in risk identification? Utilize predictive analytics and Monte Carlo simulations to forecast potential risks effectively.
- How can emerging trends strengthen risk management? Incorporate AI technologies and real-time monitoring to identify and mitigate risks proactively.
- What common pitfalls should be avoided? Don’t ignore small risks, overlook internal challenges, or neglect expert insights, as these can escalate if unaddressed.
If you Google “why projects fail” you’ll get several pages of articles and resources, including 5 reasons why project work plans fail and how to avoid them here on Wrike. A lot of the reasons are procedural, relating to scope definition, methodology, and communication, for example, but there is a common theme: an inadequate risk identification process.
Poor risk management isn’t just an issue that impacts big companies. Smaller businesses are prone to the same types of mistakes and their consequences, which can be just as (if not more) catastrophic for them. Project risk identification is not just for enterprises but a practice that should sit at the core of any business’s modus operandi.
Keep reading to learn the ins and outs of risk identification, including its lifecycle, importance, and the common pitfalls to avoid. Plus, you’ll learn how organizations like Gwynnie Bee use Wrike to manage and mitigate risks effectively.
What is risk management?
Risk management is the process of identifying, tracking, and managing potential risks that can impact the overall health and reputation of a business. The Association for Project Management (APM) in the UK describes it well: “Risk analysis and risk management is a process that allows individual risk events and overall risk to be understood and managed proactively, optimizing success by minimizing threats and maximizing opportunities and outcomes.”
Without buy-in from the top, proper stakeholder engagement, and a disciplined approach to risk identification and management, a project will carry a higher risk of failure.
The lesson here is to tackle risk at the very start of a project and let your learnings inform decisions relative to scope, process, and resourcing. Consider issues that come up time and again across projects, such as fixed price contract risk, or risk related to certain times of year for customers. Our “How to make a risk management plan” article covers this and includes examples you can refer to.
Remember this too — risk management is not just a process but about culture as well. As Tom Wilson, former Chief Risk Officer for Allianz, reminds us:
Risk management is a culture, not a cult. It only works if everyone lives it, not if it’s practiced by a few high priests.
Tom Wilson, Chief Risk Officer, Allianz
On a higher note, there are also risks that can benefit a project. For example, a potential change in an organization’s policy could remove red tape and save you time. These are typically referred to as opportunities, while negative risks represent threats. You can learn more about this here: What are positive risks in project management?
What is the risk identification lifecycle and process?
Diving deeper we find risk identification, which is the first step of the risk management process. We’ve described step one in our project risk assessment guide: “Create a list of every possible risk and opportunity you can think of. If you only focus on the threats, you could miss out on the chance to deliver unexpected value to the customer or client.”
Notice how the latter part of the definition makes a strong case for including positive risks in your planning — take every opportunity to delight stakeholders. The Project Management Book of Knowledge (PMBOK® Guide) explains that a risk management plan should include a detailed risk statement for each risk. This statement should cover:
- The cause of the risk
- When the risk might occur
- The impact of the risk on the project’s goals
So, how do you go about identifying risks? There are different frameworks for this and you should choose one that best fits your organization’s working practices and resourcing. The Project Management Institute (PMI), for example, published a comprehensive guide that explains its model in detail. This may be overkill if you’re working on a simple project or within a small organization but worth understanding nevertheless.
Let’s consider context first. Much like a project within a project, the risk identification lifecycle is a process that delivers key elements of an overall risk management plan. The risk identification process itself follows a defined structure and is elaborated progressively through six stages:
- Template specification
- Basic identification
- Detailed identification
- External cross-check
- Internal cross-check
- Statement finalization
How to identify risks in project management
For brevity, we’ll focus on the initial three steps as they cover risk identification specifically (while the remaining steps are about validating and formalizing findings against the overall project’s scope).
Template specification
This is a risk statement based on feedback about causes, effects, impacts, areas of risk, and events. A structured template helps you capture this in a consistent way.
Basic identification
Answering two questions about potential risks: why or why they occur, and whether they have been experienced before. The former can be captured via a SWOT analysis exercise while the latter is a statement, ideally referenced from a project post-mortem or lessons learned library.
Detailed identification
This step is more time-consuming than the previous ones but also delivers the detail you need to properly assess risk. PMI identifies five tools to use:
- Interviewing
- Assumptions analysis
- Document reviews
- Delphi technique
- Brainstorming
Once you’ve completed these steps you’ll need to categorize risk in the next one — the external cross-check step. We’ve covered this in our article on understanding risk breakdown structure.
Step five is the internal cross-check, which maps risks to corresponding elements in the scope of work. At this point, you will start forming a view of what project elements are riskier than others and what mitigation strategies to adopt.
The final step, statement finalization, packages findings in a series of diagrams covering risky areas, causes, and impacts.
Tip: Use a tool like Wrike to maintain a risk register spanning all of your projects that you can refer to whenever you start a new one.
Risk identification techniques
Interested in learning more about advanced risk identification techniques? Here are five techniques you can use to mitigate risks for your next projects.
1. Predictive analytics
Predictive analytics uses data — yes, all those numbers and facts from past projects — to guess what might happen in the future.
How does it work? Gather all the data you can from previous projects. This might include things like how long tasks took, the problems you faced, and even the tiny details you might not think matter. Then, you use software that analyzes this data to spot patterns.
Let’s say you run a small business that sells handmade crafts online. By looking at your past sales data, predictive analytics could help you determine which products will likely sell out during the holidays. This means you can make more of these items in advance, and boom — less stress during the holiday rush!
2. Monte Carlo simulations
Monte Carlo simulations are a way to predict different outcomes based on random variables. If that sounds a bit like gambling, it’s because this method was named after the famous Monte Carlo Casino in Monaco!
You start with what you know about your project — like costs, timelines, and resources. Then, you plug these into software that randomly changes these values (like dice rolling in a game). It repeats this thousands of times, and each time it records what happens.
This technique helps you see all possible outcomes and their likelihood. For instance, if you’re running a marketing campaign, Monte Carlo simulations can show you different budget scenarios.
- What happens if the ad cost goes up?
- What if the audience engagement is lower than expected?
This method lets you plan for different possibilities and manage your budget better.
3. Risk audits
A risk audit involves bringing in someone from outside your project to thoroughly examine your work and spot any risks you might have missed. An expert checks all your plans, processes, and outcomes and assesses them for risks.
The idea is to find any weak spots before they become big problems. If someone identifies a small issue in your plan early on, you can fix it before it becomes a disaster. Plus, it shows your team and clients that you’re serious about making the project successful.
4. Delphi technique
The Delphi technique is a method for gathering information and opinions from a group of experts without them needing to confront each other. Basically, it helps collect honest and unbiased feedback because no one knows who said what.
How does it work? You send out a series of questionnaires to a panel of experts. The questions are all about potential risks in your project. These experts fill them out anonymously and send them back. You compile the answers, summarize them, and then send out questionnaires based on those summaries. This goes on until the answers start to show a pattern or consensus.
5. Failure mode and effects analysis (FMEA)
FMEA is a step-by-step approach for identifying all possible failures in a design, a manufacturing or assembly process, or a product or service. You start by listing every single thing that could fail. For each failure, you ask:
- What would happen if this goes wrong?
- How likely is it to go wrong?
- How bad would it be if it did?
Then, you rate these failures to determine which ones need the most attention. This helps you focus your energy on fixing the big stuff before it causes trouble. Using FMEA means you catch problems early, which can save a ton of time and money. Nobody wants a last-minute scramble or a failure after everything’s done.
Emerging trends in risk identification
As projects become more complex, new trends and technologies naturally emerge. Here’s a look at some of the trends shaping risk identification today:
Artificial intelligence (AI)
AI technologies are transforming risk identification by automating the analysis of large datasets. By learning from historical data, these systems can identify complex patterns and predict potential risks. For instance, AI can forecast logistical issues in construction projects by analyzing past incidents related to supplier delays or weather disruptions.
Real-time monitoring
Advances in technology now allow for real-time monitoring of risks using sensors and other IoT (internet of things) devices. For example, in construction projects, sensors can monitor structural health or environmental conditions, sending alerts when potential risks are detected. This immediate data helps project managers make swift decisions to address issues before they escalate.
Cybersecurity
As more project operations use digital tools, the importance of managing cybersecurity risks has escalated. Project managers increasingly prioritize the security of their digital infrastructures, implementing robust cybersecurity measures to protect sensitive data and prevent breaches that could derail project timelines and budgets.
Common pitfalls in risk identification and how to avoid them
Why do some projects fail despite careful planning? Identifying and managing risks in projects can be tricky, and certain obstacles often complicate this important task. Here are some common pitfalls to avoid in risk identification:
Ignoring small risks
It’s easy to dismiss small risks as insignificant, but these can add up or evolve into larger problems over time. To avoid this, make it a habit to regularly review and assess all identified risks, regardless of their size.
Overlooking internal risks
Often, teams focus too much on external risks, like market changes or supplier issues, while forgetting about internal risks, such as team conflicts or resource limitations. You should incorporate internal assessments into your risk review process and consider factors like team morale and workload distribution.
Confirmation bias
This occurs when you only seek out information that supports your existing beliefs, leading to blind spots in risk identification. Actively seek diverse perspectives and encourage independent risk assessments.
Lack of expert input
Failing to consult with experts can result in missing critical insights, especially in complex projects. Regularly engage with industry experts and stakeholders throughout the project to avoid this. Their specialized knowledge can help identify risks your team may not know, ensuring a more comprehensive risk management approach.
Failing to update risk assessments
Risks are not static; they can change as a project progresses. However, some teams neglect to update their risk assessments regularly. To avoid this, you should schedule periodic reassessments throughout the project lifecycle. This allows you to account for new risks that may arise and adjust your plans accordingly.
Want to avoid project pitfalls like the pros? Use Wrike.
Common pain points in risk identification
Are you struggling to spot risks in your projects before they become real issues? Here are some common pain points in risk identification and how to address them:
- Pain point: Difficulty in early detection
- Solution: Implement predictive analytics and AI tools that analyze historical data to foresee and flag potential issues before they manifest.
- Pain point: Data overload
- Solution: Use integrated project management tools that organize and prioritize data effectively, helping managers focus on the most critical information.
- Pain point: Updating and tracking risk
- Solution: Employ real-time monitoring tools and maintain a dynamic risk register that updates automatically as new data comes in.
- Pain point: Communication barriers
- Solution: Use a collaborative work management platform that enhances communication flow between stakeholders, ensuring everyone is informed and engaged in the risk management process.
- Pain point: Complexity in risk analysis
- Solution: Adopt a structured risk assessment framework like FMEA, which breaks down risks into manageable parts and makes the analysis more straightforward.
- Pain point: Cybersecurity threats
- Solution: Prioritize cybersecurity within the risk management plan and use specialized software to protect project data and infrastructure.
Risk identification example
PMI’s “Pulse of the Profession 2020” report, which surveyed over 3,000 project professionals, senior executives, and directors, sheds more light on risk management. It reveals that 25% of projects falter because risks are not identified or mitigated effectively, leading to unforeseen issues that could have been managed.
Here are a couple of risk identification examples, the first one based on PMI’s methodology outlined above and the second one captured in an online risk register.
Risk identification example 1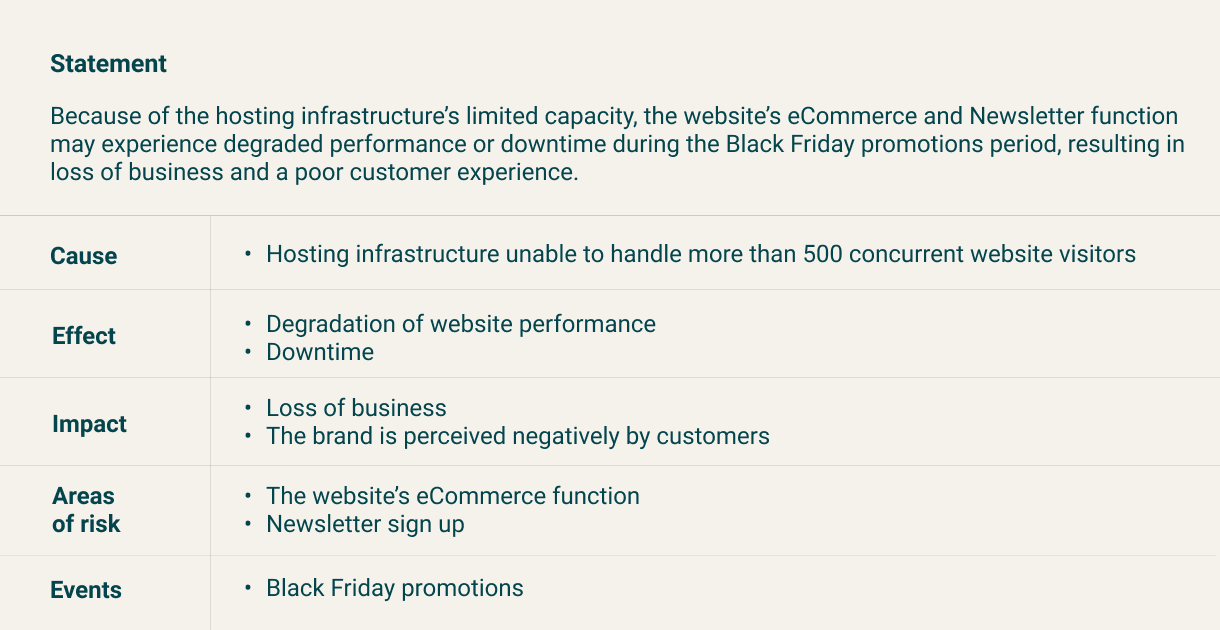
Risk identification example 2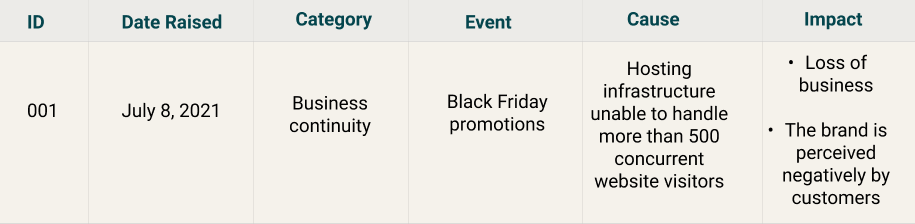
The two examples are not necessarily alternative approaches. Rather, the first one is a sample risk identification template, and the second one is a risk register holding the same information.
By using an online project management tool it becomes much easier to manage both processes and give visibility to stakeholders.
How to make a risk management plan
Think of the risks you have identified as the foundation blocks of your risk management plan. In one of his Medium posts, Alan Zucker, Founder of Project Management Essentials, shared:
I have seen many projects derailed because assumptions were never documented or validated. Or risks were identified, but a response strategy was never created.
Alan Zucker, Founder, Project Management Essentials
This insight is important as you set up your plan, which typically includes the following elements:
- Risk identification
- Risk evaluation
- Assignment of risk ownership to project team members
- Risk responses
- Plan to constantly monitor for new risks and address them appropriately
By the time you have completed the risk identification step, you will be able to refer back to detailed information for each to evaluate them, assign ownership, and determine responses. You can analyze the risk using qualitative analysis. According to the standard guidelines for risk management in portfolios, programs, and projects, you can perform a qualitative analysis by looking at several key factors. These include:
- How seriously the risk could impact the project’s goals
- How manageable the risk is
- When the risk might occur
- How the risk is related to other risks
- The chance of the risk happening
This type of analysis is usually shown in a chart called a risk assessment matrix.
|
Impact or Severity |
||||||
|
Probability or Likelihood |
Insignificant |
Minor |
Moderate |
Major |
Catastrophic |
|
|
Very Likely |
Low-Medium |
Medium |
Medium-High |
High |
High |
|
|
Likely |
Low-Medium |
Low-Medium |
Medium |
Medium-High |
High |
|
|
Possible |
Low |
Low-Medium |
Medium |
Medium-High |
Medium-High |
|
|
Unlikely |
Low |
Low-Medium |
Low-Medium |
Medium |
Medium-High |
|
|
Very Unlikely |
Low |
Low |
Low-Medium |
Medium |
Medium |
|
However, work doesn’t stop once you’ve done the risk analysis. As the project progresses, you’ll need to monitor for and identify new risks. Risk ownership plays an important role here too, so make sure you’ve defined processes for communication and escalation. This brings us to the next question: who should oversee risk?
Who should oversee risk?
Large organizations appoint risk managers at the C-suite level and often form risk committees with representatives from different departments, who report back to the CEO and the board. Large organizations will have their risk governance regularly audited by external parties too.
The model becomes increasingly “risk governance lite” for smaller businesses but project risk identification and management should always be a priority.
It’s good practice to assign responsibilities at the very start of a project, mapping roles with responsibilities. Here’s what this could look like for larger organizations.
- Project sponsor: Has overall responsibility for a project and signs off on the risk management plan
- Project manager: Has overall responsibility for risk management, including communication and escalation
- Risk owner: A member of the project team or a stakeholder who is an owner of individual risks
- Risk committee: Has a view of risk across every project of an organization
In smaller organizations, you’ll see business owners wearing the project sponsor hat, and they’re less likely to have risk committees. The more diligent ones will cover risk just as effectively by streamlining the process.
Risk identification template
A template to list and analyze risks is an easy way to ensure you and your stakeholders are on the same page. With Wrike’s project risk analysis template, your team can quickly and easily identify potential risks and their scope, mitigate risks by prioritizing certain tasks, and implement RAID (risks, assumptions, issues, and dependencies) logs into your workflow.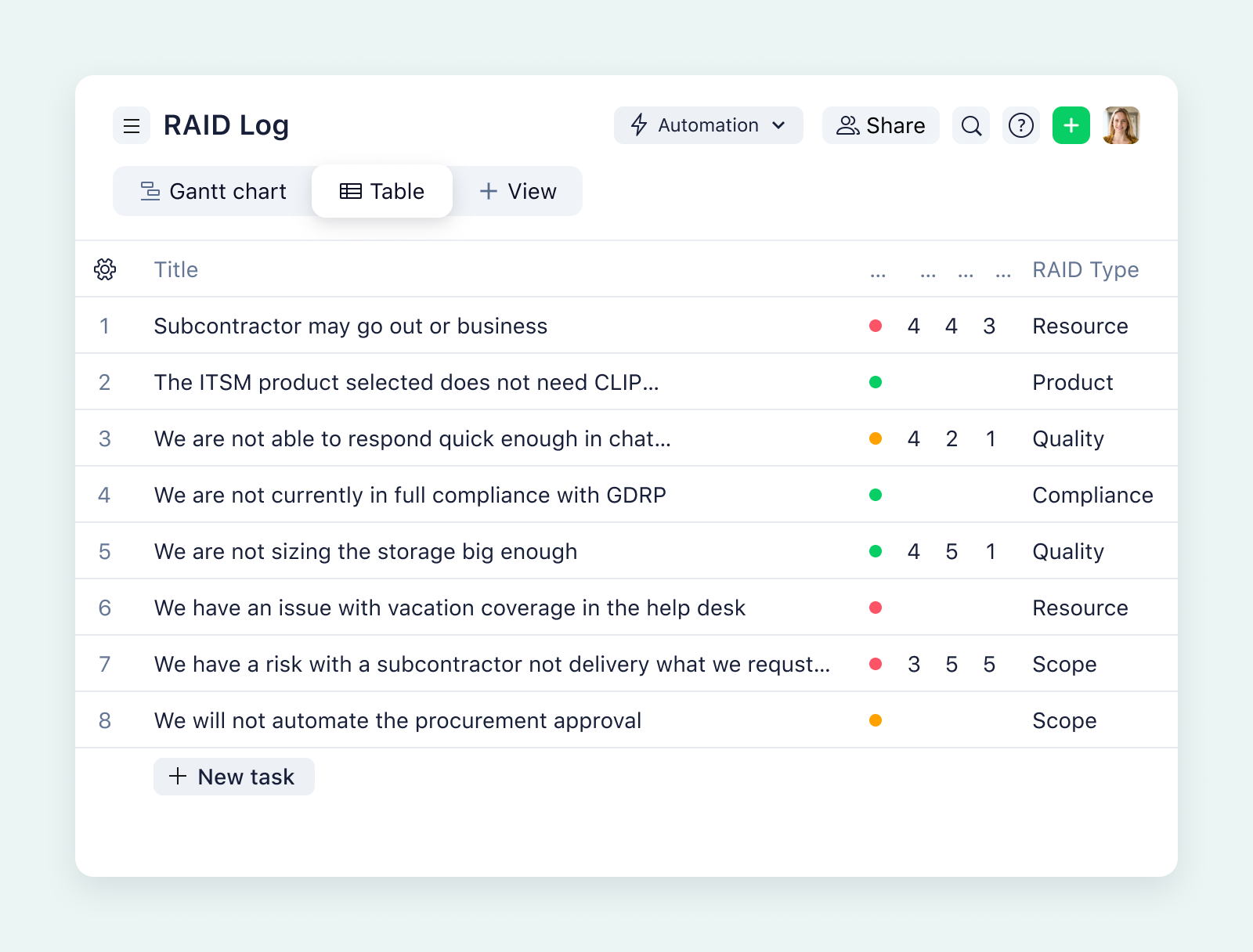
Wrike’s template comes with prebuilt request forms to help you create detailed RAID entries when they arise. As you can see from the table above, each risk, along with its impact, probability, and proximity scores, are all listed in one place, so your team can capture and mitigate risks at a glance.
Using Wrike to manage (and mitigate) risks
By now, you know that risk management is a critical component of project management.
It’s therefore surprising to learn that many larger organizations rely on outdated tools like documents, spreadsheets, and emails to manage risk. This presents all kinds of risks if you think about it. How many times has a file gone missing or an older version updated and circulated?
By using a modern, versatile, and powerful project management tool like Wrike you gain efficiency and reduce risk at the same time. Here’s how:
- Your risk identification and management process is centralized and easily accessible
- You can design workflows to facilitate steps in your risk management plans
- You can add multiple levels of categorization and tagging to risks to search them across multiple projects
- You get alerts for high-priority risks
- You’re always up to date and can run reports at the touch of a button
- You communicate and collaborate in real-time
Case study: Gwynnie Bee
Gwynnie Bee, a trendsetting clothing rental service for plus-size women, faced growing pains as it rapidly expanded. Managing a high volume of tasks across different locations became a formidable challenge. Quality suffered and project visibility was poor, affecting operations and customer service.
A potential risk identified was inadequate staffing on key dates for delivering heavy equipment at the new distribution center. Using Wrike, the brand could assign staff tasks and monitor these assignments in real time, ensuring no gaps in personnel coverage that could jeopardize operations.
By integrating Wrike into its processes, Gwynnie Bee enhanced its operational efficiency and reduced its order processing time by a stunning 60% within a year. The successful implementation of Wrike helped Gwynnie Bee manage risks effectively and scale strategic projects. In one year, the number of strategic projects completed increased significantly from 27 to 40, highlighting the effectiveness of its refined risk identification and management processes.
Wrike allows us to plan a project with enough detail that we really reduce the risk … of the project not going correctly.
Phillip Hoffman, Senior Program Manager
Key takeaways
TL;DR? Here are the main points you should take away from this article:
- Risk identification is the first step of the risk management process. You must identify risks before continuing with your risk management plan.
- Larger organizations often rely on dedicated risk committees to identify and track risks.
- There is a variety of techniques — such as predictive analytics and Monte Carlo simulations — you can use to foresee and prepare for potential risks.
- Adopt emerging trends such as AI and cybersecurity measures to stay ahead in risk management.
- Never underestimate the importance of small risks; they can escalate quickly if ignored.
- Ensure access to and use expert insights to enhance risk identification and mitigation strategies.
- Stay informed about compliance and regulatory changes that could impact risk assessment.
- Use real-time monitoring software, such as Wrike, to identify and respond to emerging risks quickly.
Ready to see how Wrike can help manage project risks of all sizes? Get started today with a free two-week trial.




