Wrike Security Overview
Last update: October, 2025. Wrike, Inc.
Wrike Security Overview
Last update: October, 2025. Wrike, Inc.
Wrike is the leading collaborative work management platform helping organizations around the globe align work with the most important business objectives, create new efficiencies, and drive results.
We are dedicated to making our Wrike the most secure and reliable collaborative work management platform on the market. We are committed to protecting your personal and company data, and ensuring secure collaboration within our platform, which is why we continue to invest in the security of our services to not only meet, but exceed industry standards.
Security has always been a top priority and we have relentlessly pursued a robust and mature security strategy since the day the company was founded in 2006. Below is an overview of Wrike’s security strategy, which includes a comprehensive approach across five key categories: Physical, network, system, application, and people.
Wrike hosts its mission-critical servers in dedicated cages within data centers located in the US and EU:
These facilities feature 24/7 manned security, fully redundant power backup systems, physical access controls, biometric authentication systems, extensive seismic bracing, the latest in early-detection smoke and fire alarms, and digital surveillance systems. All server and network components are continuously monitored by internal Wrike staff and by the colocation providers.
Wrike's Disaster Recovery infrastructure resides in Google’s Cloud Platform for both the US and EU regions, having great scalability and security with SSAE16 / ISAE 3402 Type II, ISO 27001, FedRAMP, PCI DSS, and HIPAA and other certifications.
Access to each system, network device, and application is limited to authorized personnel, and login details within the event logs are reviewed on a continual basis.
Over years of continuous service, Wrike has consistently met or exceeded a 99.9% uptime, ensuring customers can access their tasks and projects when needed without interruption. If Wrike is temporarily unavailable due to technical reasons or scheduled maintenance, you can log in to the standalone, read-only replica of Wrike to access all your data at https://login.wrike.com/login/?read.
Our databases use real-time replication to offsite locations with a 15-minute recovery point objective (RPO), guaranteeing availability across redundant and geographically diverse servers, with 99.9% of changes synchronized within 10 seconds. Wrike also provides regular database backups according to the following schedule:
The combination of daily, weekly, and monthly backups ensures a robust data recovery strategy. The seven-day daily backup retention is critical for addressing immediate data loss issues, while the longer weekly and monthly backups provide additional layers of protection and historical data restoration options.
Recovery will be automatically performed by the Wrike CloudOps team in the event of critical issues. Customers can request their account recovery if significant data problems occur due to client actions. Customers are advised to contact Technical Support in that case. Recovery requests will only be processed for Enterprise or Pinnacle accounts with 200 or more seats, acknowledging the complexity and size of these accounts. Manual restoration by the customer is not deemed feasible under these circumstances.
Wrike uses industry-standard network protection procedures, including network segregation using VLAN’s, firewall and router technologies, intrusion detection and prevention systems, centralized log aggregation, and alert mechanisms. These procedures are used in conjunction with secure connectivity, including secure channels and multi-factors for authorized systems operations group personnel. This allows us to prevent, detect, and promptly remediate the impact of malicious traffic and network attacks.
Ongoing internal network security audits and scanning gives us an overview for quick identification of impacted systems and services. According to our in-house patch management policy, operating systems, software, frameworks, and libraries used in Wrike infrastructure are updated to the latest versions on a regular basis. Whenever a vulnerability in a product used by Wrike or a high or critical vulnerability is publicly reported, prompt actions are taken to mitigate any potential risks for our customers — we apply hotfixes and patches promptly when available and/or implement pro-active mechanisms like configuration of firewalls or IDS/IPS.
Wrike uses operating system-based and custom integrity check services to ensure the integrity of all critical files and system objects. A quick response to any potential unauthorized changes to the system helps insure our customers are using Wrike-approved application services.
An in-depth Application Security Lifecycle process is fully integrated into Wrike's Software Development Lifecycle (SDLC), including:
Each user in Wrike has a unique, password-protected account with a verified email address. The password is validated against password policies and stored securely using a strong hashing algorithm with a unique salt for every password. 2-Factor Authentication is available as an additional security measure to protect Wrike accounts. Wrike also supports multiple methods of federated authentication, including Google Open ID, Azure, Office 365, ADFS and SAML2 to conveniently and securely gain access to a Wrike account leveraging corporate credentials. Wrike also offers advanced security settings that allow customers to manage Network Access Policy and Password Policy. More details can be found in our Help Section.
The Wrike Support Team is always happy to assist you with any Wrike-related issues. If troubleshooting or verifying an issue requires support to access your account, that access can be granted only by you. This is enabled by a system-generated security token that you provide to our support team, allowing support to delve deeper into solving your problem for a limited amount of time. This systemic approach ensures additional confidentiality for your data stored in Wrike.
A Wrike account administrator manages and controls individual user rights by granting specific types of user licenses. Details about various user licenses, roles, and authorization controls in Wrike are documented in our Help Section.
Customer data, including tasks and folders, can only be accessed by other users within your Wrike account if those items were specifically shared with them, or if the items were placed in shared folders.
Wrike offers flexible data access control setup by allowing admins to configure Customized Access Roles, which offer the choice of more than 20 different permissions for user actions in Wrike, and can be used to specify user or group access levels to certain folders, projects and tasks. Selective sharing can be enabled to not follow the default of inheriting sharing settings, giving greater access control over specific subfolders and Subprojects. Wrike’s Access Reports allow administrators to holistically review user access to sensitive data.
Wrike enables customers to get a report with up-to-date account activity information, including authentication events, changes in authorization and access controls, shared folders and tasks, and other security activities. The same report is available through a REST API that allows for integration with Security Information and Event Management (SIEM) and Cloud Access Security Broker (CASB) systems.
Wrike uses Transport Layer Security (TLS) 1.2 with a preferred AES 256 bit algorithm in CBC mode and 2048-bit server key length with industry-leading modern browsers. When you access Wrike via web browser, mobile applications, email add-in, or browser extension, TLS technology protects your information using both server authentication and data encryption. This is equivalent to network security methods used in banking and leading e-commerce sites.
All users’ passwords, cookies, and sensitive information are reliably protected from eavesdropping. User files uploaded to Wrike servers via both web application and API are automatically encrypted with AES 256 using per-file keys. If someone were to gain physical access to the file storage, this data would be encrypted and impossible to read directly. These encryption keys are stored in a secure key vault, which is a separate database decoupled from the file storage layer. In addition, all Wrike workstations and servers are encrypted at rest using file system encryption where AES 256-bit is used.
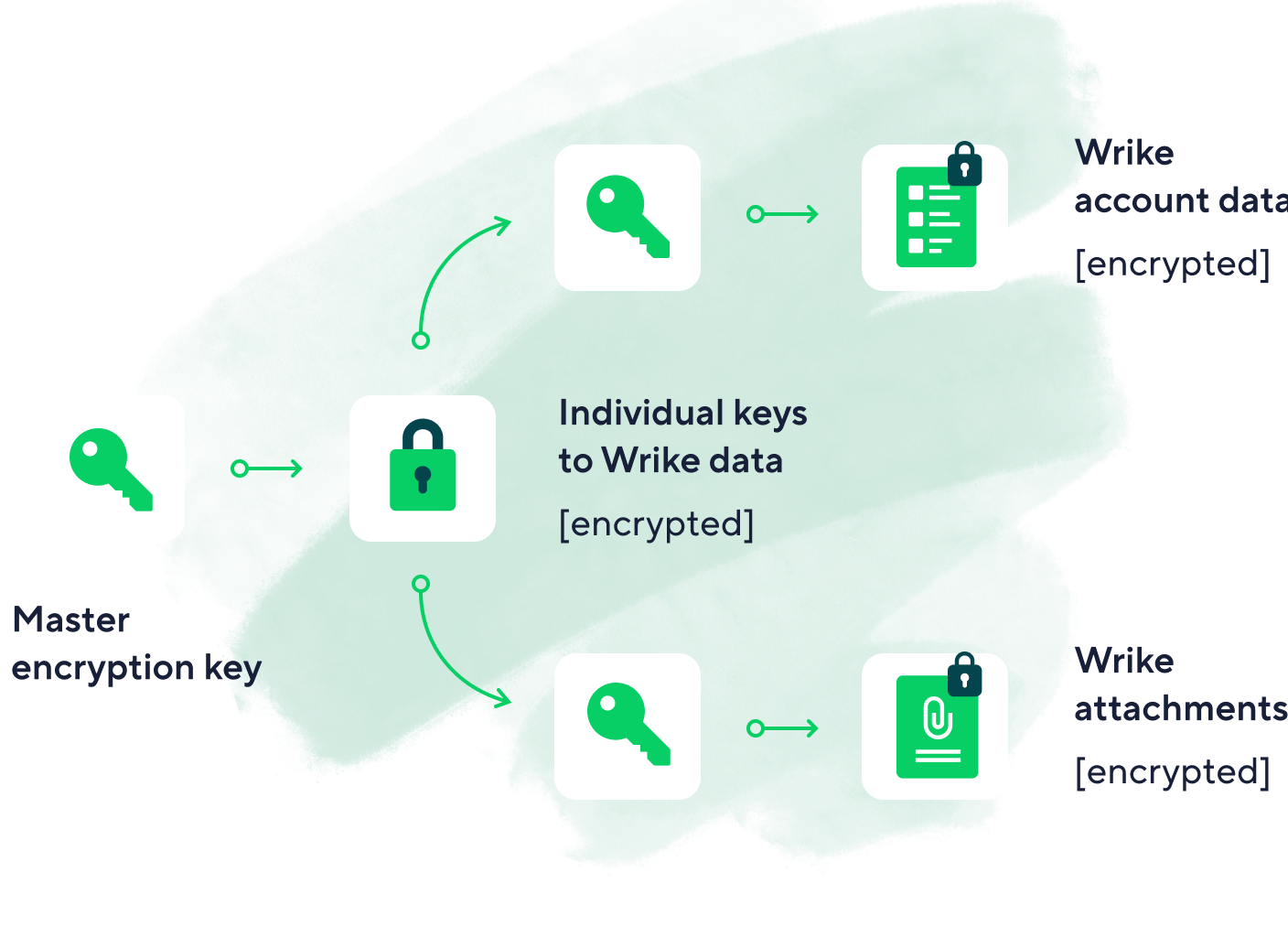
Wrike Lock
The Wrike Lock add-on for Wrike’s Enterprise plan adds an additional layer of security by encrypting the encryption keys for Wrike workspace data (including tasks, folders, projects, workflows, and comments) and Wrike attachments with a master Customer-Managed Key (CMK), which is stored in Amazon Web Services’ Key Management Service (AWS KMS). By using AWS KMS, the master encryption key is fully owned and controlled by the customer and stored outside of Wrike, and access to Wrike data can be monitored or revoked by the customer only. The diagram demonstrates this.
Additionally, Wrike supports an emergency recovery procedure to decrypt Wrike data in the event a customer’s master CMK is lost or unavailable. This is achieved by encrypting Wrike’s data encryption keys with an asymmetric RSA key pair generated by the customer, where the public key is sent to Wrike to set up the procedure and the private key remains with the customer (the private key can be stored in a hardware security module).
Your Wrike workspace is accessible via Android and iOS applications, which inherit security functionality from Wrike’s web-based application. These applications also have additional security features like encryption at rest, certificate pinning, checking against rooted/jailbroken devices, and application-level protections using a PIN code or fingerprint.
Wrike offers a backup tool which allows customer to make a backup of their data and download it to a local machine. Details about user-performed account backup can be found here.
You can also safely recover accidentally deleted items from Wrike’s recycle bin. If a user is deleted by mistake, there is a possibility to recover the deletion (including some of their tasks) if you contact us within 3 business days. Some user account information can be recovered for up to a month after deletion.
Designing and running datacenter infrastructure requires not only technology, but also a disciplined approach to processes. This includes policies about escalation, management, knowledge sharing, risk management, and day-to-day operations. Wrike’s security and operations teams have years of experience designing and operating data centers, and we continually improve our processes over time. Wrike has also developed best-in-class practices for managing security and data protection risk. All of these elements are essential parts of Wrike’s security culture.
Only a limited set of employees have access to our datacenter and the data stored in our databases. There are strict security policies for employee access, all security events are logged and monitored, and our authentication methods and data are strictly regulated. Access to production requires establishing a VPN channel, multi-factor authentication, a one-time password, and a personal certificate.
We limit access to customer data to employees with a job-related need, and require all these staff members to sign a confidentiality agreement. Accessing customer data is only done on an as-needed basis, and only when approved by the customer (i.e. as part of a support incident) via a support token, or under authorization from senior management and security for the purposes of providing support, maintenance, or improving service quality.
This baseline is intended to demonstrate our commitment to industry practices regarding the secure, transparent, and fair use of AI within Wrike features.
Development and maintenance of Wrike’s Work Intelligence® solution are organized the same way as all our solutions and offerings. The Wrike product complies with SOC 2 Type II, ISO 27001, ISO 27017, ISO 27018, ISO 27701, and TX-RAMP Level 1 certifications.
Wrike’s ML-powered solutions pass an enhanced security review including checks against listings in OWASP Machine Learning Security.
All AI projects undergo threat modeling and security reviews on all stages, from design to implementation.
Generative AI features, such as AI content creation, are powered by Microsoft Azure OpenAI Service. The data is securely housed with enterprise-grade controls, such as opt-in, access rights, and moderation for harmful, illegal, and IP-protected content, and is protected by an enterprise-friendly legal framework. Customer data is not used to improve Microsoft and other third-party products and services, including machine learning models. The manner in which Microsoft Azure OpenAI Service processes data and the relevant protections and security measures are set out in Microsoft's Data, Privacy, and Security Policy for the Azure OpenAI Service.
General data, such as anonymized search-related historical usage statistics, may be used for Wrike machine learning model training, but specific data, such as user names and associated task descriptions, is never stored or used for model training.
You can find more details in our AI Addendum.
Wrike’s Work Intelligence features are designed as stateless. This means that by turning on the AI-powered features, users don’t have any direct communication with databases containing customer data. The functionality can be turned on and off without impacting the privacy of historical data.
The content generated with Wrike’s Work Intelligence features can be checked, edited, or used at the time it is created. All use cases require a user action to verify the output in order that all outputs are explainable, meaning their decisions can be understood and approved by humans.
Wrike prohibits the use of sensitive PII and certain categories of regulated and confidential data within any kind of AI powered solutions across the whole company. Wrike’s Work Intelligence is designed under the same approach.
We continue to monitor worldwide AI subject matter working groups and regulations to follow the principles of human centricity and oversight, accountability, fairness, transparency, data protection, and security to make sure even our most security-concerned customers can give the new features a try.
Learn more about our AI ethics policy, here.
GDPR & CCPA: For customers who request it, we have a Data Processing Addendum and CCPA Addendum that outlines the obligations Wrike has in its role as a provider of the Wrike Service to Customer. This may include obligations related to the General Data Protection Regulation (Regulation (EU) 2016/679) (GDPR), Standard Contractual Clauses (SCCs), and California Consumer Privacy Act (CCPA) as well as other applicable laws.
HIPAA: The Health Insurance Portability and Accountability Act provides security provisions and data protection for safeguarding medical information. If Wrike processes Protected Health Information (PHI) on behalf of either a Covered Entity or a Business Associate (both known as “roles” under HIPAA), then Wrike has a Business Associate Agreement that meets industry standards and requirements as well as the HIPAA Security Rule. This is available upon request.
U.S. CLOUD Act: The CLOUD Act allows for government requests for data regardless of storage location, but only through a strictly regulated process that requires a valid court order, legal review, and is limited to specific criminal investigations. Wrike adheres to the strict legal and procedural requirements of the CLOUD Act, ensuring that any government data request is subject to independent court approval and comprehensive legal safeguards. We are committed to protecting our customers’ privacy by challenging conflicting requests, complying with GDPR, and continually investing in robust security controls and European data infrastructure.
The Wrike Privacy Policy has been carefully cultivated to address your privacy concerns and your rights with regards to your personal data. If requested, Wrike will also provide a Data Protection Addendum, which describes our data practice.
Compliance

This independent, third-party examination assesses the nature and effectiveness of the internal controls Wrike uses to protect customer data. Type II SOC 2 audits demonstrate Wrike’s commitment to taking a mature, robust, and secure approach to products, processes, and security as it relates to customer data.

The report is based on Type II SOC2 audit and demonstrates Wrike’s commitment to meeting security, confidentiality, availability, and privacy principles in the industry.

This independent, third-party certification ensures Wrike has an end-to-end security framework and a risk-based approach to managing information security. The certification illustrates Wrike’s dedication to a best practice security strategy aligned with international security standards.

This certification ensures Wrike as cloud service provider has a direct focus on the information security aspects of cloud computing and a system of rigorous controls in place that are specific to cloud services.

This certification ensures Wrike has measures to protect Personally Identifiable Information (PII) in accordance with the privacy principles in ISO/IEC 29100 for the public cloud computing environment.

This certification ensures Wrike as PII Data Processor maintains a robust privacy information management system to ensure that effective controls are in place not only to meet the requirements of GDPR, CCPA (California Consumer Privacy Act), but also best practices are utilised to fulfill the requirements of many other privacy legislations.

Wrike has passed the third party stage of this certification (Level 1 of CSA STAR). This demonstrates that Wrike, as a cloud service provider, has addressed issues critical to cloud security as outlined in the CSA Cloud Controls Matrix. It also demonstrates that Wrike has been assessed against the STAR Capability Maturity Model for the management of activities in cloud security control areas. CSA STAR is an independent, third-party assessment of cloud service provider security. The technology-neutral certification leverages the requirements of ISO/IEC 27001:2022 management system standards and focuses on specific cloud-service requirements.

Wrike has successfully completed the Texas Risk and Authorization Management Program's security assessment and authorization process.

Enterprise Grade Security
If you have any security questions and concerns, please contact our team, and they will provide you with additional security artefacts and external reports confirming our security maturity.
